Key Takeways
- SMS phishing combines SMS and phishing which essentially means using SMS to get people to share their confidential sensitive information
- SMS starts from target selection followed by messaging and then using the stolen information
- Smishing can be of multiple types like account information fraud, bank fraud, tax scams etc.
- Multiple things can be done to identify and avoid smishing attacks including detection tips and prevention strategies
- Cybersecurity firms and SMS service providers play a crucial role in protecting businesses from such attacks
What is SMS Phishing or Smishing?
SMS Phishing, commonly referred to as "Smishing," is a type of cyber-attack that utilizes SMS (Short Message Service) or text messages to deceive individuals into divulging sensitive information.
The term combines "SMS" with "phishing," reflecting its nature as a phishing attack carried out via text messaging or SMS sent by businesses. Smishing is particularly insidious because it exploits the personal and direct nature of text messages. Cybercriminals send seemingly legitimate texts, often impersonating trusted entities, to lure victims into sharing personal, financial information, clicking on malicious links, or downloading harmful software.
This is very common in use case of OTP SMS as SMS verification services are used by almost all businesses across industries and geographies.
How Smishing Works:
- Target Selection: Attackers choose their targets randomly or based on specific data, like details from previous breaches.
- Crafting the Message: The deceptive text is created to provoke an emotional response (urgency, fear, curiosity) and typically includes a call to action. SMS does not allow any media in its composition so there’s none in these attacks. That is also being changed with RCS, for which we sometimes receive sent as SMS via server as read receipts.
- Message Delivery: Using various technologies, the smishing message is sent to the targeted individuals.
- Interaction: The victim interacts with the message, leading to potential data collection or malware deployment.
- Use of Stolen Information: Acquired data is used for malicious purposes or further targeted attacks.
Types of Smishing Attacks:

- Account Verification Scams: Fraudulent alerts from banks or service providers asking to verify account details. This is usually done by sending an OTP SMS.
- Prize or Lottery Scams: Messages claiming the victim has won a prize, often leading to theft of information or money.
- Tech Support Scams: Fake warnings about device or account issues, leading to potential data theft or charges.
- Bank Fraud Alerts: Phony alerts from banks about unauthorized transactions or suspicious activities.
- Tax Scams: Messages around tax season claiming to be from tax agencies, often involving refunds or penalties.
- Service Cancellation: Claims of service or subscription cancellations due to payment issues, directing users to phishing pages.
- Malicious App Downloads: Promotions for apps that lead to the installation of malicious software.
Smishing versus Phishing and Vishing:
- Smishing: Uses SMS or text messages sent by businesses using SMS APIs.
- Phishing: Primarily uses email and malicious websites.
- Vishing (Voice Phishing): Employs voice calls to deceive individuals into giving away sensitive information
Examples of Smishing Attacks:
Smishing attacks can vary greatly, but they often involve luring victims with promises of money, alarming them with fraudulent security alerts, or masquerading as legitimate organizations. A typical message might prompt users to verify a bank transaction or claim a prize by clicking a malicious link or providing personal information. Attackers use social engineering techniques to make these messages appear credible and urgent.
A similar attack in context of businesses is SMS pumping where a lot of messages are sent automatically, adding to the SMS bills. The same can be identified with unusual patterns on SMS dashboards.
How to Identify and Prevent Smishing Attacks
Detection Tips:
- Be wary of messages offering quick money or requesting sensitive information.
- Avoid responding to unknown or suspicious numbers.
- Utilize telecom services to report and block spam messages.
Prevention Strategies:
- Technological Solutions: Employ SMS filtering, multifactor authentication, and anti-phishing tools.
- Organizational Solutions: Conduct regular cybersecurity training, establish reporting mechanisms, and perform simulated smishing tests.
- Individual Solutions: Avoid clicking suspicious links, verify sources independently, and stay updated on the latest smishing tactics.
The Role of Cybersecurity Firms:
Cybersecurity firms offer advanced solutions to protect against smishing and other cyber threats. They provide unified protection across email, social media, and mobile channels, employ advanced threat intelligence, and offer risk analysis and customized recommendations to mitigate risks. Their tools are designed to detect and counteract a wide range of cyber threats, ensuring comprehensive defence against smishing and related cyber-attacks.
Conclusion
Smishing is a pervasive and constantly evolving threat that targets individuals through their most personal communication channels. Understanding how these attacks work, recognizing the common types, and employing strategies for detection and prevention are key to safeguarding personal and financial information.
As cyber threats continue to grow in sophistication, staying informed and vigilant is more important than ever. Whether as individuals or organizations, adopting a multi-layered defence strategy and promoting cybersecurity awareness can significantly mitigate the risks associated with smishing and ensure a safer digital environment for all.







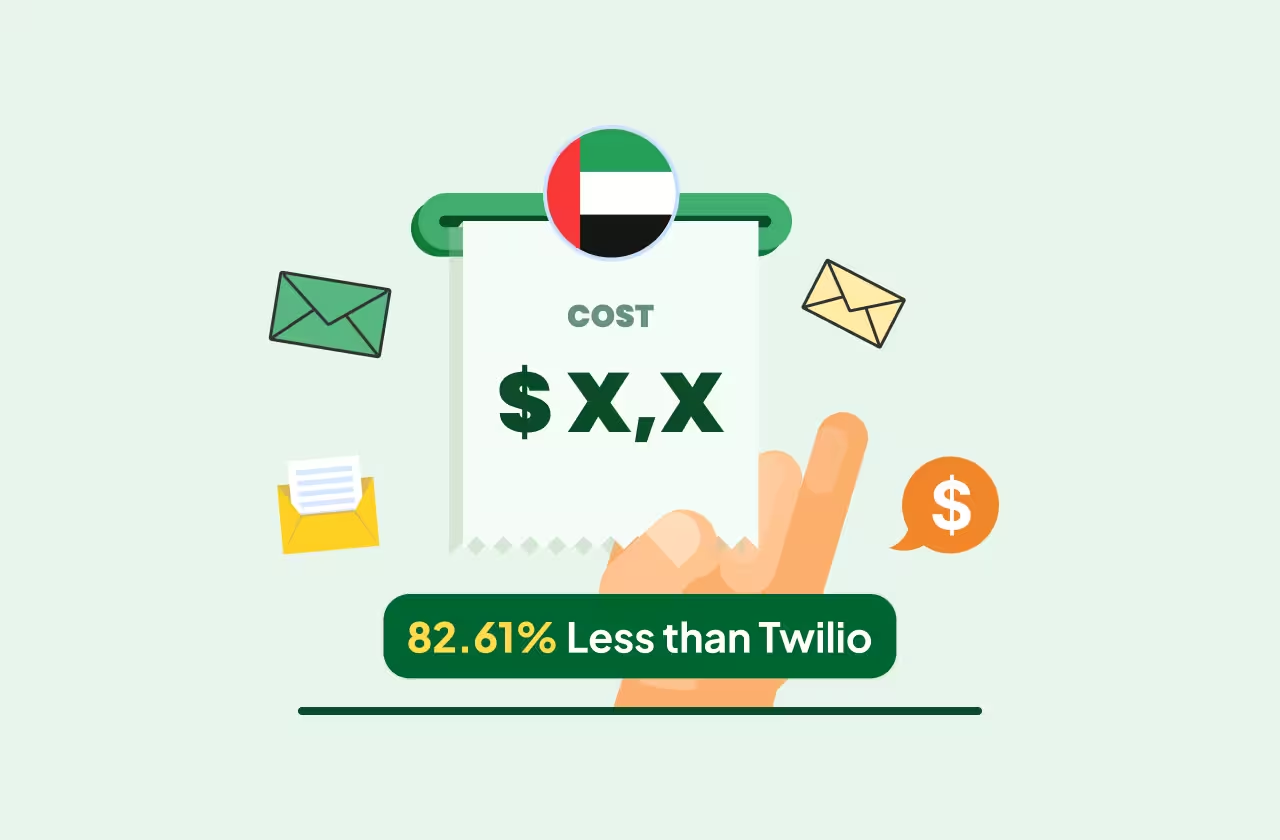

.avif)